- Activity 8.1: Setting Up a Firewall in a Linux-Based Operating System
- Figure 2: Status check
- Figure 3: Reloading and updating
- Activity 8.2: Installing and Configuring Suricata
- Figure 4: Upgrading Packages in Linux
- Figure 5: Installation of Suricata on Kali Linux
- Figure 6: Monitoring real-time logs
- Figure 7: Editing the Suricata Configuration File
- Activity 8.3: Comparing IDS and IPS
- Figure 9: IDS and IPS
- Activity 8.4: Exploring PIDS and VMIDS
- Figure 10: Intrusion Detection System
- Activity 8.5: Investigating Anomaly and Signature Detection
- Anomaly Detection Using Expert Systems
- Advantages & Disadvantages
- Signature Detection Using Supervised Machine Learning
- Advantages & Disadvantages
- Activity 8.6: Setting Up a Honeypot
- Figure 11: Honeypot capturing an attack log
- Figure 12: Attack attempt details from the main machine
- Activity 8.7: Analyzing Security Measures for University of Derby
- Figure 13: Analyzing Security Measures
- Activity 8.8: Advising on IDS/IPS Products
- Figure 14: IDS/IPS Products
- Activity 8.9: Investigating VPN Encryption Algorithms
- Figure 15: VPN Encryption
- Activity 8.10: Designing an Integrated Security System
- Integrated System for Securing a Medium-Sized Company
- Network Security: Firewalls and IDS/IPS
- Data Encryption and Secure Communication
- Authentication and Access Control
- Endpoint Security and Malware Protection
- Backup and Disaster Recovery
- Employee Training and Awareness
Activity 8.1: Setting Up a Firewall in a Linux-Based Operating System
A Firewall in a Linux based operating system is an important aspect to manage and regulate the flow of traffic into and out of a network based on set policies. This involves defining the firewall setting and rules with the aid of the UFW (uncomplicated Firewall) or even Iptables in order to regulate the network access to the services. The images presented below show how the firewall setting and check can be done in the environment of Linux.
The first action in implementing a firewall is checking the status of the latter. First of all, it is necessary to turn off or check the position of the firewall and to know which rules are activated (Aradi and Bánáti, 2025). The picture above depicts the command which checks the existing firewall and shows its current status. In the case it is not active, the firewall has to be activated to meet the security policy of the network.
For detailed step-by-step help, visit Assignment Help UK for cybersecurity assignment support.
Figure 1: Installing and Updating UFW
(Source: Self-created)
The next process that needs to be undertaken concerns the enabling of this firewall, provided the status of the former is positive. From the following image below, you are able to identify the command used to start this firewall type: Enabling the firewall facilitates the checking of any traffic that is deemed to be prohibited by the firewall while at the same time, it allows all the rightful traffic through. When the computer is booted up, there is a need to check on the firewall service in order to ensure it is up and this confirms that the security policies are running.
Figure 2: Status check
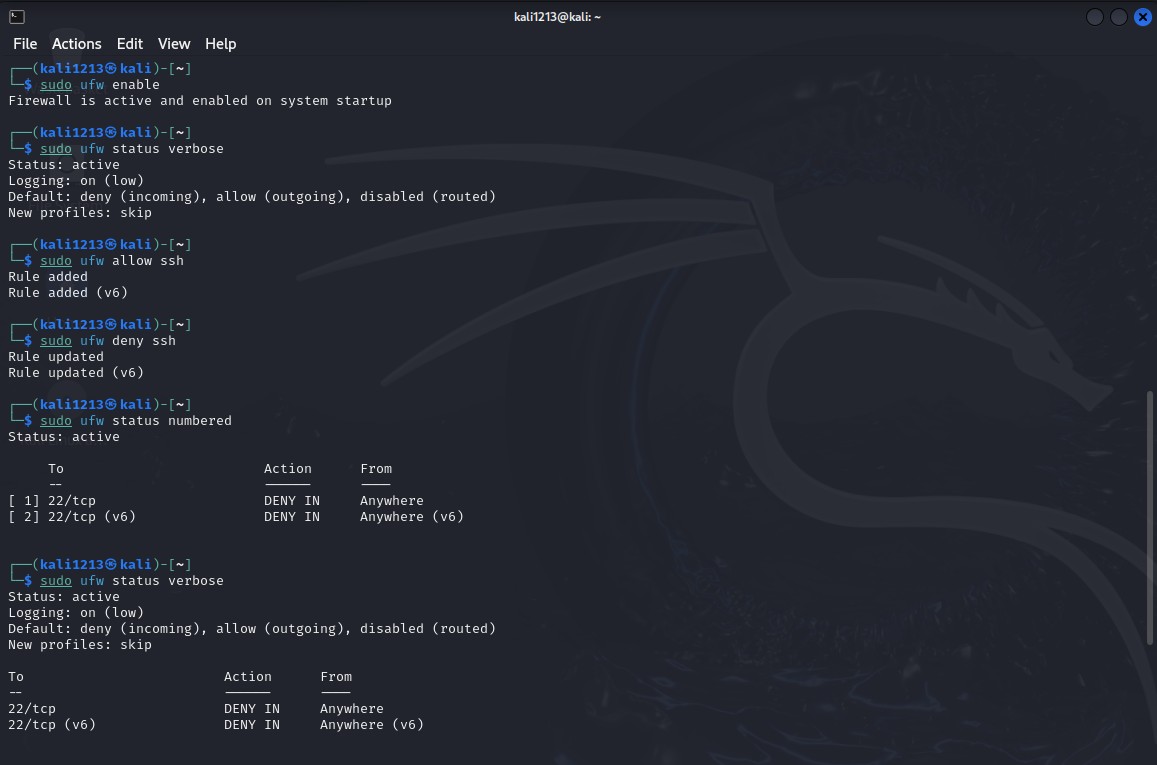
(Source: Self-created)
To address this, once the firewall is enabled particular rules must be defined regarding the flow of traffic in the networks. The figure is drawn to elongate the explanation of the rules that should be added to allow or eliminate particular types of connections. For most organizations, explicit permission is required so that services such as SSH, HTTP, HTTPS can be permitted to enable a provision to access resources and web servers. The other prominent observations on the image are the passed-out commands that allow only SSH traffic for secured connection to the system. That is why one of the aspects of firewall configuration includes the ability to prevent unwanted traffic. A significance of the image is to point out the use of commands to block access to certain port numbers (Trisolino, 2023). Filtration of the services which are not needed and the services which have high risk factors decrease the chances of being attacked. From the picture mentioned above, it is possible to understand how to deny the connection with any unauthorized source and allow only those addresses which are allowed to make connections with the system.
Figure 3: Reloading and updating
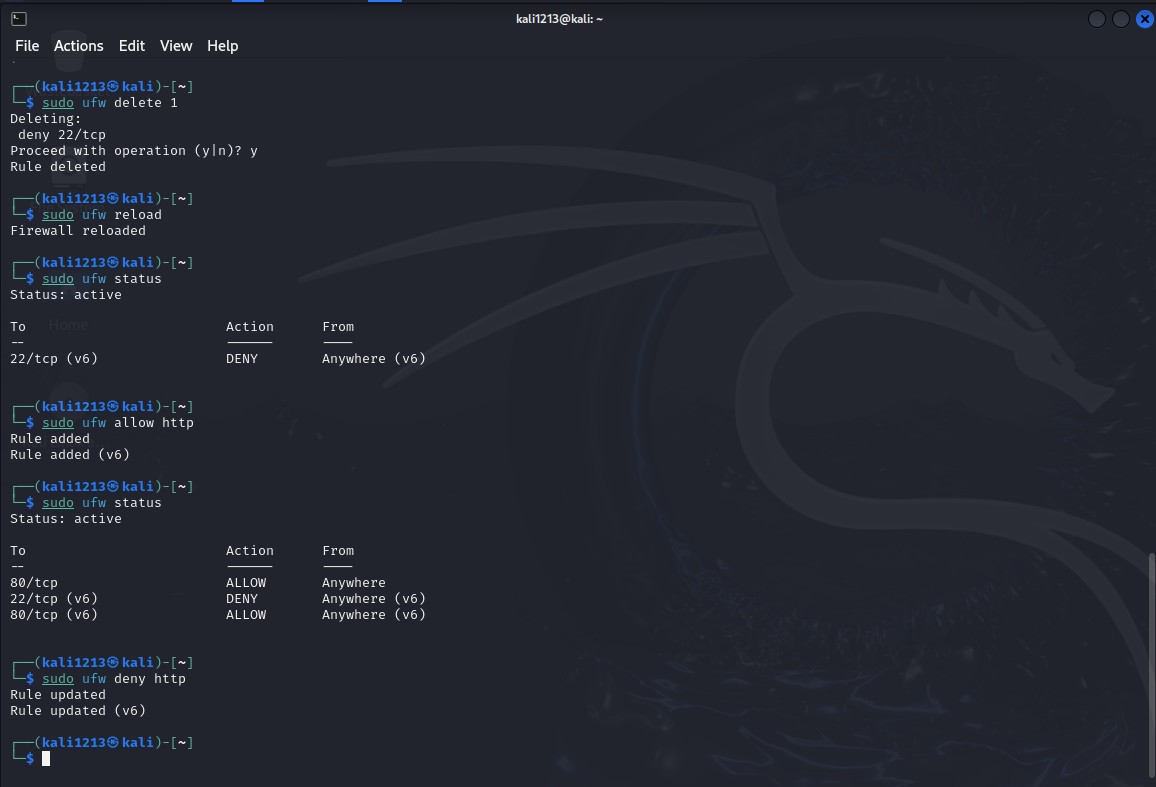
(Source: Self-created)
Afterwards, it is important to reload the firewall to incorporate the change which was just configured. The last of them represents the command for reloading or restarting the firewall so that the newly set policies are activated. It is crucial to reload the firewall after the alteration of the rule set to ensure all the changed configurations are implemented. The configuration rule check is an essential procedure to perform to ascertain the functionality of the firewall. The image given above shows the firewalls’ command that can be used to determine which services and ports are opened or closed (Sharma, 2024). Performing this enables the confirmation that the rules set when configuring the device dovetail with the security requirements on the device as well as checking to ensure that there are no other unintended configurations. Lastly the firewall configuration is tested to know whether it is working as required or not. The image illustrates probe traffic like ping or telnet, in order to ensure that such traffic is blocked and such that traffic is allowed (Franco et al., 2021). This step ensures that the firewall is blocking traffic depending on the rules set in place properly.
Reference List
Aradi, Z. and Bánáti, A., 2025, January. The Role of Honeypots in Modern Cybersecurity Strategies. In 2025 IEEE 23rd World Symposium on Applied Machine Intelligence and Informatics (SAMI) (pp. 000189-000196). IEEE.
Trisolino, A., 2023. Analysis of Security Configuration for IDS/IPS (Doctoral dissertation, Politecnico di Torino).
Sharma, D.S., 2024. Enhancing False Positive Detection in IDS/IPS Using Honeypots: A Case Study with CSE-CIC-2018 Dataset [online]
Franco, J., Aris, A., Canberk, B. and Uluagac, A.S., 2021. A survey of honeypots and honeynets for internet of things, industrial internet of things, and cyber-physical systems. IEEE Communications Surveys & Tutorials, 23(4), pp.2351-2383.
Activity 8.2: Installing and Configuring Suricata
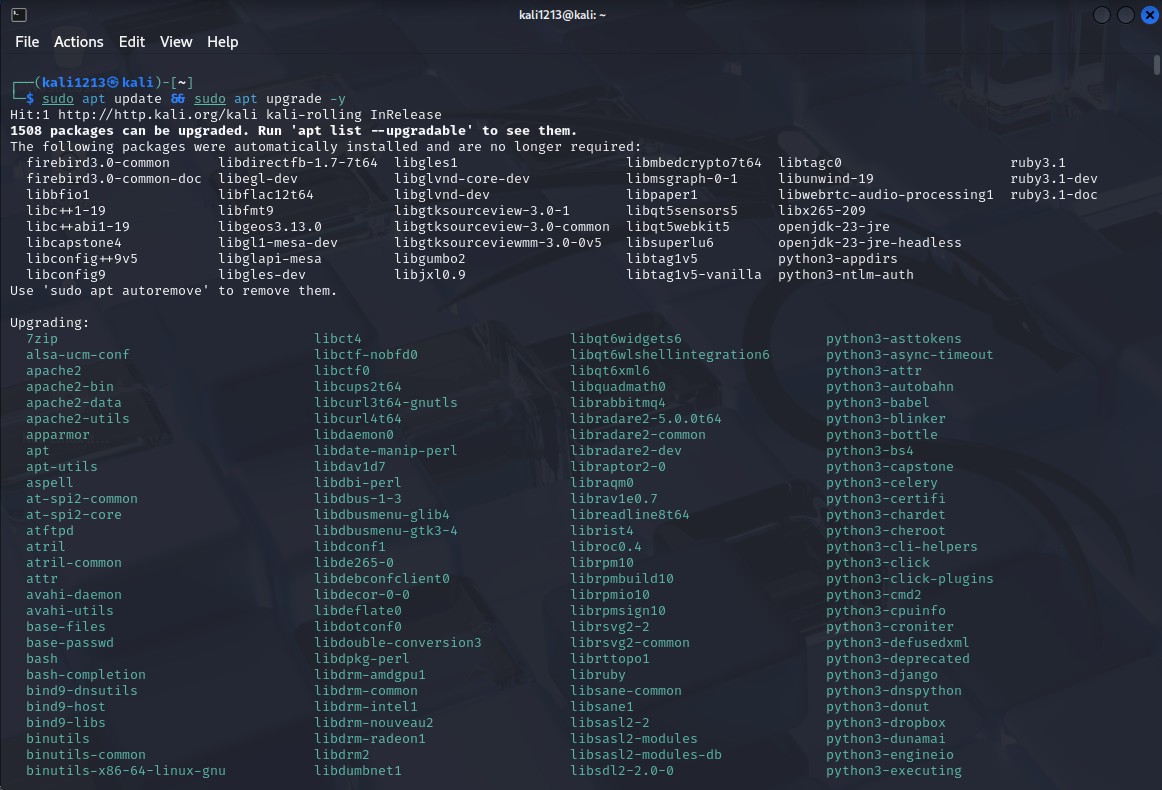
Figure 4: Upgrading Packages in Linux
(Source: Self-created)
Figure 5: Installation of Suricata on Kali Linux
(Source: Self-created)
Figure 6: Monitoring real-time logs
(Source: Self-created)
Figure 7: Editing the Suricata Configuration File
(Source: Self-created)
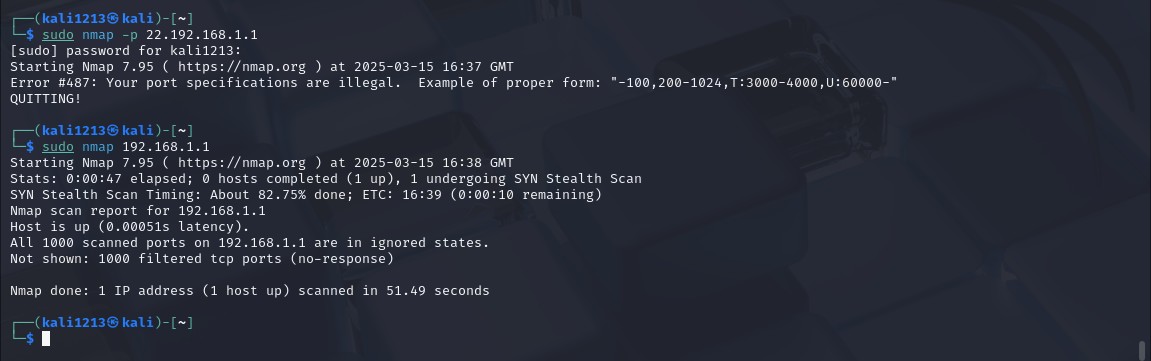
Figure 8: Nmap Scan
(Source: Self-created)
Activity 8.3: Comparing IDS and IPS
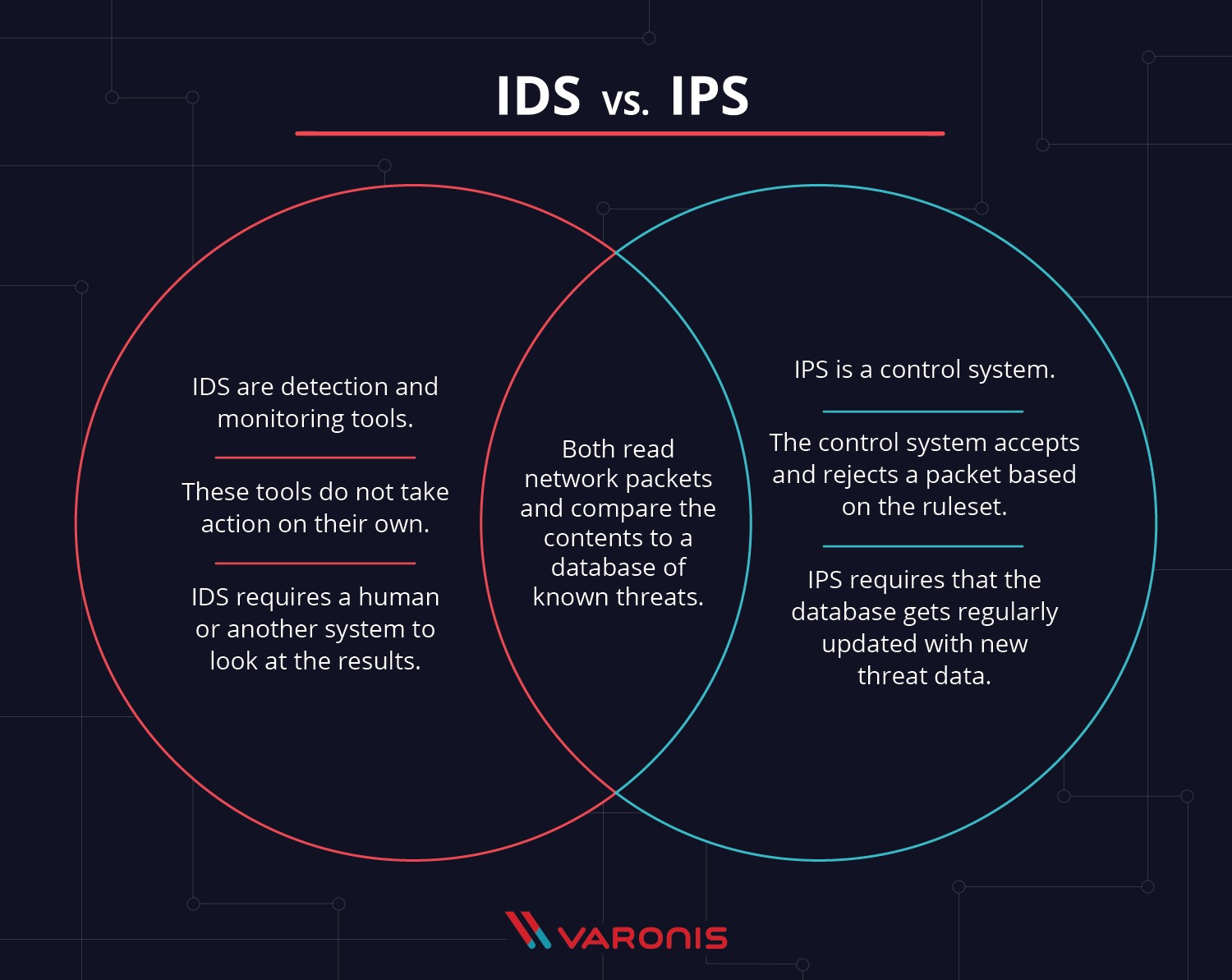
Figure 9: IDS and IPS
(Source: https://customerthink.com)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are two extremely important aspects to any network security solution because they address two key aspects of security in a different manner.
Algorithms and Functionality
IDS mainly employs signature based, anomaly based, or both of them in order to detect intrusions. It has alarms when there is an occurrence of the event of interest; however, it does not intervene immediately (Franco, 2022). IPS, however, has the capability to investigate the same algorithms and can even counter the malicious traffic by providing measures like dropping the packets or closing the malicious connections.
Location in the Network
IDS and IPS are sections of software within a network and depending on where they are positioned within the network, the amount of protection is limited to. HIDS/HIPS are installed at host level and work with events such as file system, process and system call. As such, they offer ample security to a single host but only up to a certain set level (Achari, 2024). On the other hand, Network-based IDS/IPS (NIDS/NIPS) are normally positioned behind the routers or firewalls & mimic traffic across the different devices analyzing both headers as well as the packet payload.
Cloud-based IDS/IPS
Due to the advancement in the cloud computing era knowledge based CIDS/CIPS have gradually evolved. They are related to both host based and network based systems that are used to monitor the virtualization resources of SaaS, PaaS and IaaS. It can discover patterns all over the world and provide concentrated safeguard for the cloud-based applications and systems.
Hardware and Pricing Considerations
When it comes to the price of IDS and IPS, the choice depends on the range of the product and installation type. A host-based system costs less than any other and is only capable of operating on individual hosts (Luntovskyy, 2023). Therefore, network and cloud-based solutions are relatively costlier than standalone solutions because they cover larger areas and have other intricate formations.
Reference List
Franco, J.R., 2022. Honeypot-based Security Enhancements for Information Systems.
Achari, A., 2024. Advanced Cybersecurity Tactics. Educohack Press.
Luntovskyy, A., 2023. Advanced Networking and Cybersecurity Approaches. In Reliability Engineering and Computational Intelligence for Complex Systems: Design, Analysis and Evaluation (pp. 79-98). Cham: Springer Nature Switzerland.
Activity 8.4: Exploring PIDS and VMIDS
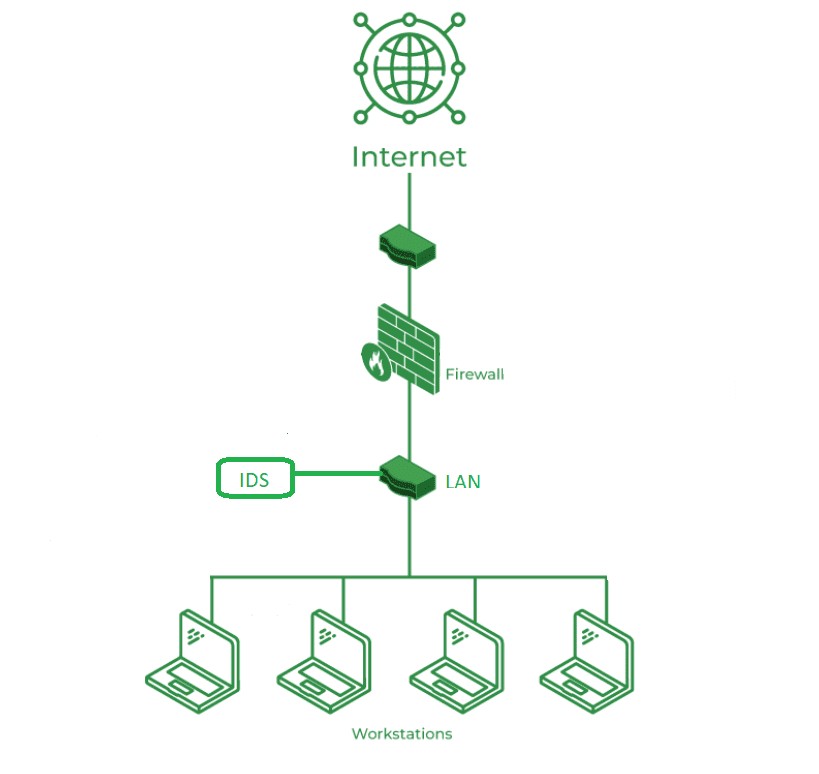
Figure 10: Intrusion Detection System
(Source: https://media.geeksforgeeks.org)
Perimeter Intrusion Detection System (PIDS)
A Perimeter Intrusion Detection System (PIDS) is therefore a system that is used to check the outer perimeters of a particular network or a physical area. Typically, it is used in perimeters of the network embracing the firewalls, routers, or the gateways. PIDS normally comprises physical or hardware sensors and software-based techniques that help in the identification of attempts or intrusion of the network by an unauthorized user. This can be implemented in physical as well as in virtual context work to ensure that it detects any intrusion attempts emanating from outside the network (Athukorale et al., 2025). Although PIDS appears to be a different form of IDS, it has correlation with NIDS as it is established to identify network intrusions. Therefore, it can be understood that PIDS is a specific subspecies of NIDS, which deals with the outer layer of the network.
VM-based Intrusion Detection System (VMIDS)
VMIDS are particularly developed to enable the detection of intrusions in virtual machine environments or cloud computing structures, for example, virtual machines. These systems can identify various illegitimate actions in virtual settings to increase security as normal emerging IDS may fail in distinguishing between the physical and virtual hosts. More commonly, VMIDS works by analyzing traffic inside the virtual machine or some layer of hypervisor where it aims at detecting intrusions on virtualized systems. Even though VMIDS may seem as a separate category, it is in fact a subcategory of HIDS as it is primarily centered around the host system or virtual machine analysis for any suspicious activity (Rabiul Hasan, 2024). Therefore, VMIDS can be viewed as an improved version of HIDS that is designed especially for virtual environments.
Reference List
Athukorale, N.K., Yi, C.J., Loh Zi Xin, A.Y., Qi, C.J., Yu, D.Z., Wei, J.S.J., Hady, F., Zhe, L.S., Eu, C.C. and Sindiramutty, S.R., 2025. Evaluating Advanced Cybersecurity Technologies for Cloud Environments.
Rabiul Hasan, M., 2024. Safeguarding of Financial Organization from Cyber-Attack using Next Generation Firewall (NGFW), Security Information & Event Management (SIEM) and Honeypot (Doctoral dissertation, Dublin Business School).
Activity 8.5: Investigating Anomaly and Signature Detection
Anomaly Detection Using Expert Systems
Anomaly detection is one of the techniques widely utilized in Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). There are two types of approaches to identify an anomaly: rule-based approach and statistical based approach, and expert systems that use a rule based structure are commonly used to detect an anomaly. These systems employ stored structures to keep track of behaviors that differ from the normative ones and include rule-based knowledge about the population. Most IDS experts work on the premise of seeking to identify how a system or network behaves normally, and then comparing actual activity against such a baseline (Raghul et al., 2024). If it goes beyond this, the expert system points to it as an abnormality or out of the ordinary activity.
Advantages & Disadvantages
Scalability: The expert systems can be designed to adapt easily to accommodate the various environments to enable easy identification of any strange behavior.
Expert systems are not without their risks; Since the system identifies any form of variation from the norm, there may be too many alarms and generalizations common in environments with variable activities or complex system patterns, hence technologists refer to it as false positives.
Signature Detection Using Supervised Machine Learning
In the case of IDS using signature-based detection, it depends on the patterns of attack also called signatures to detect intrusions. IDS/IPS works under supervised machine learning, which means that the system identifies between the attack and normal traffic patterns since the datasets are labeled. It narrows down to examining each current traffic and checking if it contains any similar characteristics to what the system has learned signatures from (Yang et al., 2023). This type of detection is especially effective for the cases where attacks are relatively easy to present in a database of known exploits, viruses or intrusions.
Advantages & Disadvantages
Effectiveness against Known Threats: Signature-based systems therefore boasts high accuracy when it comes to threats that are already well known, a quality that is very important when it comes to a common attack signature.
Ineffective Against Unknown Attacks: The approach cannot detect new or unknown threats (zero-day attacks) unless the signatures of the threats are added.
The major difference between expert systems and supervised learning in detection of the intrusions is in how the two systems detect intrusions. The first of them, expert systems, is designed to find out when the traffic deviates from the norm, while the second one, signature-based systems, match the traffic to known signatures of intrusions. However, IDSes based on expert systems are more flexible and capable of identifying new ones but may have some limitations of having high fake alarms and scalability issues. On the one hand, supervised machine learning and signature-based methods are accurate and rapidly identify new threats with the low false-positive rates, while, on the other hand, they fail to work with the zero-day attacks or attacks that are unknown to the system (El Kouari et al., 2025). In real life, the modern IDS/IPS system often implements both approaches; however the signature benefit is used in addition to the anomalies.
Reference List
Raghul, S.A., Gayathri, G., Bhatt, R. and Kumar, K.V., 2024, June. Enhancing cybersecurity resilience: Integrating ids with advanced honeypot environments for proactive threat detection. In 2024 3rd International Conference on Applied Artificial Intelligence and Computing (ICAAIC) (pp. 1363-1368). IEEE.
Yang, X., Yuan, J., Yang, H., Kong, Y., Zhang, H. and Zhao, J., 2023. A highly interactive honeypot-based approach to network threat management. Future Internet, 15(4), p.127.
El Kouari, O., Lazaar, S. and Achoughi, T., 2025. Fortifying industrial cybersecurity: a novel industrial internet of things architecture enhanced by honeypot integration. International Journal of Electrical & Computer Engineering (2088-8708), 15(1).
Activity 8.6: Setting Up a Honeypot
Honeypot is an intentionally created fake system to lure in attackers in order to monitor their activities. To elaborate this concept, a honeypot was deployed on a Linux VM and the realistic attacks were performed using another machine. For instance, in an experimental setup, the popular honeypot called Pentbox was installed specifically for purposes of capturing unauthorized accesses to the system over ssh. The methods followed are to create an environment by using Python virtual environment, to open SSH ports and to run Pentbox as a service.
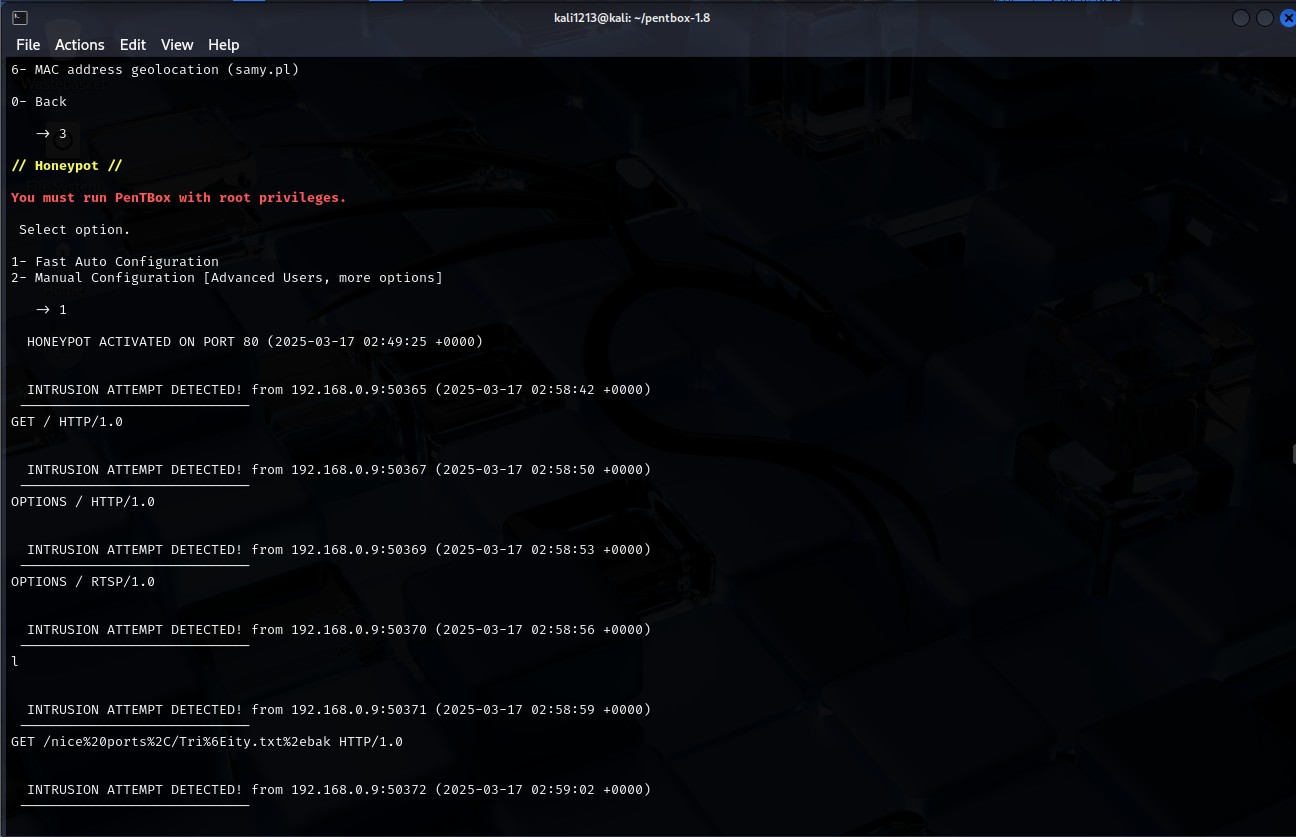
Figure 11: Honeypot capturing an attack log
(Source: Self-created)
After establishing the honeypot implementation, attempts of unauthorized SSH logins were done using tools such as Hydra. In the honeypot activity several logins wherein it captured attacker IPs and the login identification of the attackers were observed. These logs shed the beams of light regarding the characteristics of the attacks and the credential being utilized frequently (Chairopoulou, 2024). Likewise, port scanning was also done by using Nmap from another system as well. Honeypot was able to detect the scans evidence of which has been logged during the attempts showing a possibility of reconnaissance.
Figure 12: Attack attempt details from the main machine
(Source: Self-created)
This activity made an understanding of honeypots when designing cybersecurity strategies. With the help of the attacks, threats can be prevented, as well as measures to increase the level of protection can be taken. The information gathered by honeypot logs is useful to IDS and helps the security crews to adjust their tactics. However, honeypots must be placed with great caution as the intelligent attackers will know that there is a trap for them. These systems commonly known as honeypots are very useful when it comes to anticipating attacks and help to identify the trends in malicious activities that can be used for improving security measures. Their compatibility with firewalls, IDS/IPS and access control improves the security of enterprises (Albinsson and Riedl, 2021). This also drew attention to potential problems with honeypot configured, where a misconfigured honeypot may potentially expose other important systems accidentally.
Reference List
Chairopoulou, S., 2024. Cybersecurity in industrial control systems: a roadmap for fortifying operations (Master's thesis, Πανεπιστήμιο Πειραιώς).
Albinsson, F. and Riedl, J., 2021. HONEYPOT–To bee or not to bee: A study of attacks on ICS/SCADA systems.
Activity 8.7: Analyzing Security Measures for University of Derby
The University of Derby has provided for its protection and for maintaining the integrity of information technology security, several comprehensive measures. One of its critical measures towards enhancing its security aim is to employ a Security Operations Centre (SOC) equipped by KHIPU Networks. It provides round-the-clock SOC as a service, in which the threats are detected and prevented by utilizing artificial intelligence and behavioral analysis. Specifically, it is provided at a cheaper rate, though the firm lists it at one-third the cost of other vendor services. As far as the programs in the field of cybersecurity, the University of Derby has an MSc Cyber Security program that has been certified by the Chartered Institute of Information Security (CIISec). This accreditation translates to the fact that the curriculum offered in these colleges and universities meets the market requirements in cyberspace, amidst emerging threats.
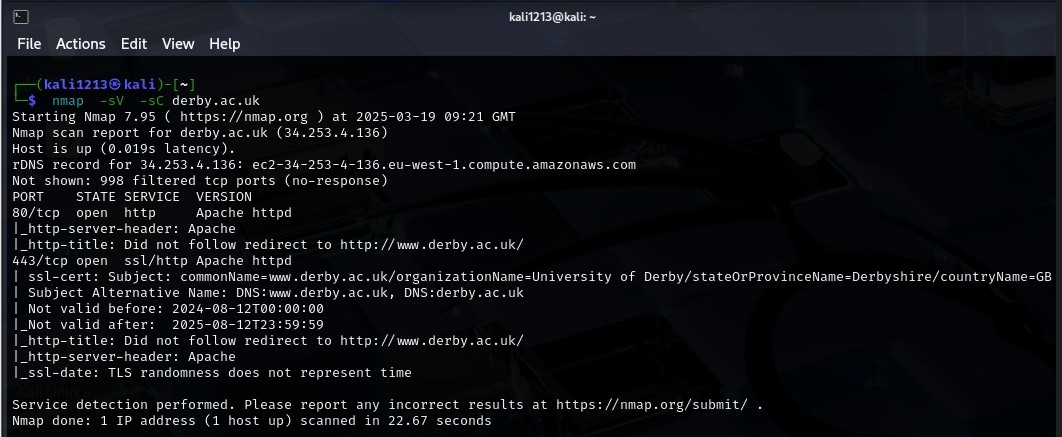
Figure 13: Analyzing Security Measures
(Source: self-made)
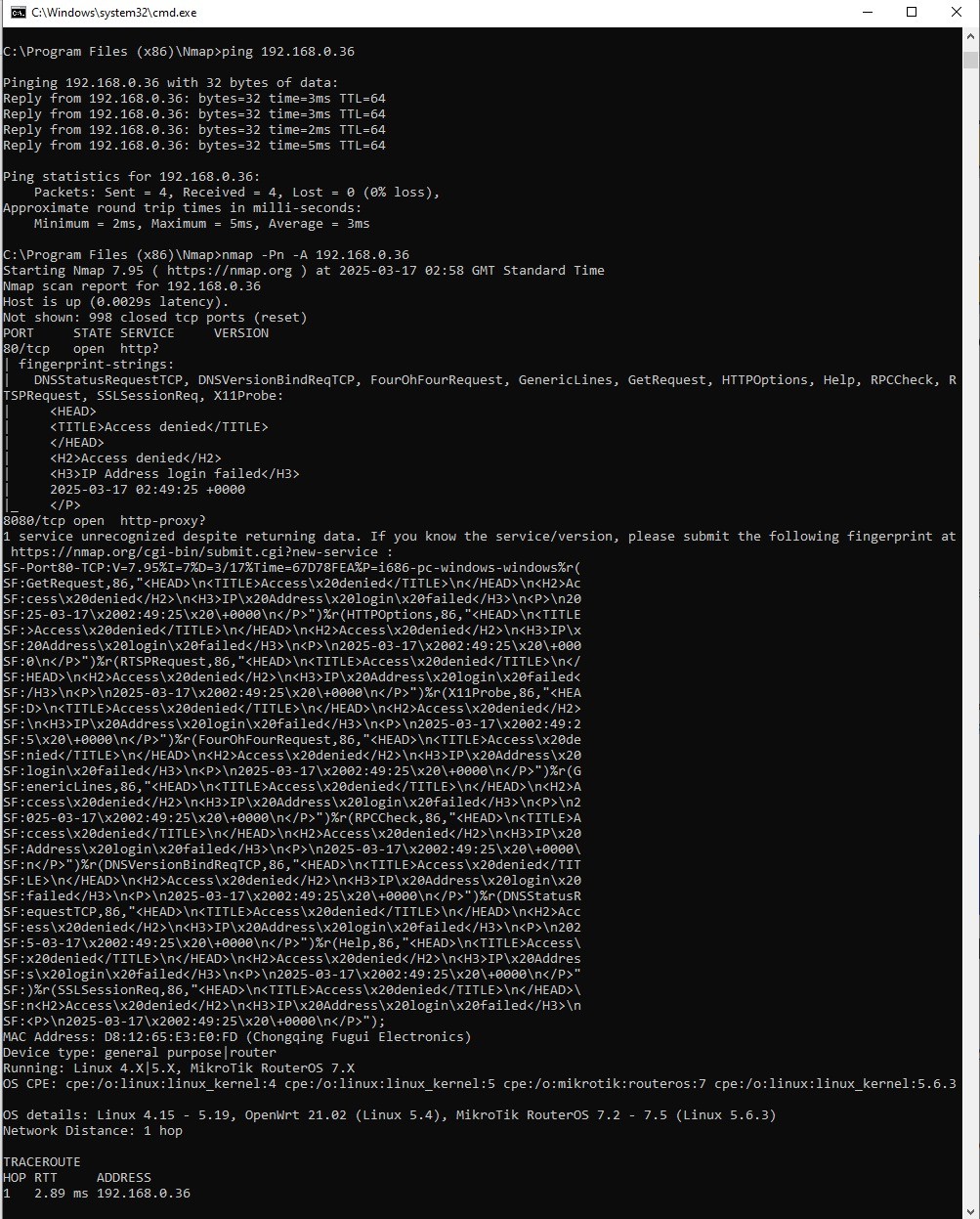
The established target is derby.ac.uk, and Nmap scan shows an open port for http and has information about the server. The scan has pointed to the use of HTTPS for the purpose of secure transfer of information, hence fits with University of Derby’s strong security features such as Security Operations Centre and accredited Cyber Security courses.
In terms of the website security, Employer uses HTTPS (HyperText Transfer Protocol Secure) that encrypts the data transmitted between the users and the website to be secure and unsuitable to be used by a third party. Pertaining to the security protocols in use, the particular implementation of HTTPS that is currently being deployed is unknown to the public, however, the University ensures that the security measures are the latest. In order to manage the new and changing threats, risk assessment and modifications are carried out as required. Additionally, the University of Derby also supports online security especially towards its members in the community. It adopts policies that are both efficient yet convenient for the users to report these matters to ensure their security is enhanced as soon as possible. This kind of precaution is useful in reducing risks likely to result from cyber threats (Abhijith and Kumar, 2021). Altogether, sophisticated protection and prevention methods, monitoring, a set of QA certified programs, and the security-aware community are essential prerequisites that University of Derby has applied to promote the safeguard and safety of its electronic resources and users.
Reference List
Abhijith, R. and Kumar, B.S., 2021, May. First Level Security System for Intrusion Detection and Prevention in LAN. In 2021 2nd International Conference for Emerging Technology (INCET) (pp. 1-5). IEEE.
Activity 8.8: Advising on IDS/IPS Products
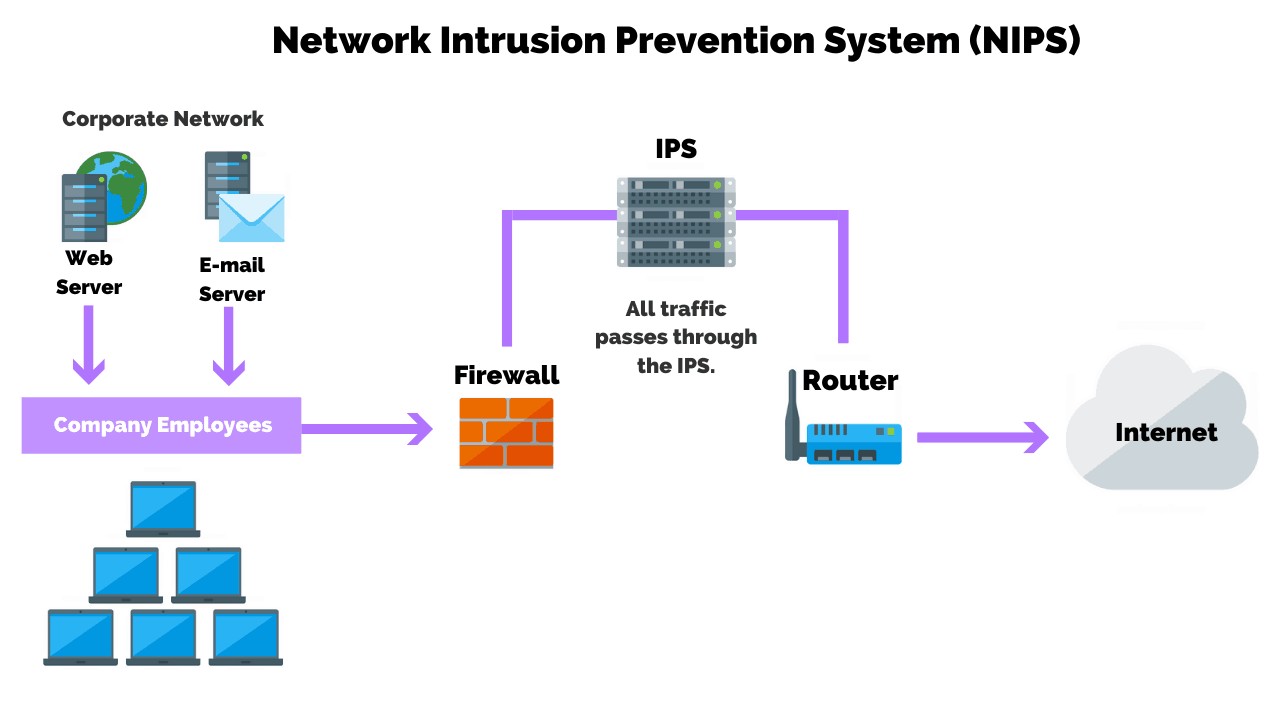
Figure 14: IDS/IPS Products
(Source: https://customerthink.com)
Recommendations for Large Organization
In the case of a large organization that operates under several branches, it is suggested to go for a blend of an IDS and an IPS. A network-based IDS/IPS (NIDS/NIPS) like Snort or Suricata should be implemented at various strategic areas of the network in order to inspect the traffic. These monitor network’s flow analyzing the packets and alerting when threats are identified in real time. In an effort to take a proactive defense approach, two important devices that can be used are the Cisco Firepower or Palo Alto Networks IPS appliances. These systems are not only used to identify and analyze malicious traffic but also to prevent them according to the set security standards (Rana and Patil, 2025). Also, there is the Hybrid IDS/IPS, host-based IDS/IPS (HIDS/HIPS) that can be implemented for the single servers and workstation.
Recommendations for Small Organization
Thus, for the small organization, which operates from two rooms, it is only reasonable to implement a less complex and less expensive option. NetFlow, for instance, is a software-based tool, which will be located at the network perimeter that can be substituted by a Network-based IDS/IPS (NIDS), such as Suricata or Snort. These are easier to manage and offer enough security to the small settings than more complicated ones (Kelly et al., 2021). Third, a HIDS/HIPS such as OSSEC can be run individually on each local machine as an additional layer of protection. Some of the solutions that are available in the cloud and easy to integrate with the business are CrowdStrike or Bitdefender GravityZone.
Reference List
Rana, M. and Patil, J., 2025. Fortifying Cyber Defenses: Leveraging Honeypots for Proactive Threat Mitigation and DoS Attack Prevention. International Journal of Computer Science & Communications (IJCSC), 10(1), pp.1-16.
Kelly, C., Pitropakis, N., Mylonas, A., McKeown, S. and Buchanan, W.J., 2021. A comparative analysis of honeypots on different cloud platforms. Sensors, 21(7), p.2433.
Activity 8.9: Investigating VPN Encryption Algorithms
Figure 15: VPN Encryption
(Source: https://networkinterview.com)
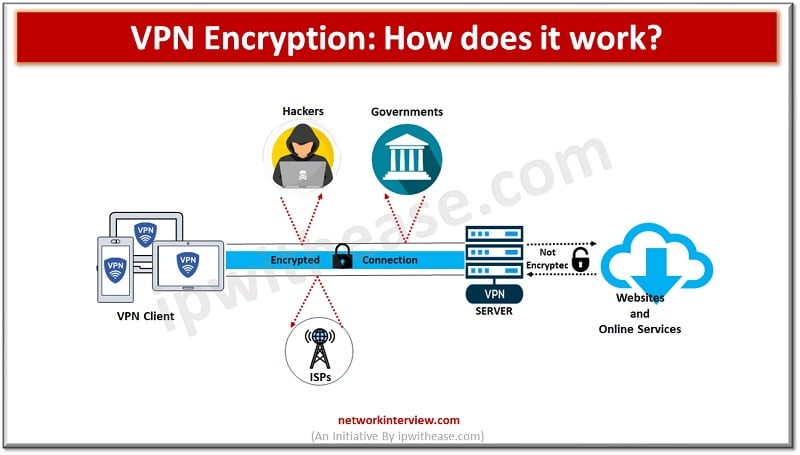
VPNs employ the use of encryption to make communication over the internet secure to prevent leakage of information by intruders. These encryption algorithms are used to ensure that any data being transmitted cannot be intercepted or altered in any way.
AES (Advanced Encryption Standard): AES is actually the most popular encryption method widely used in today’s VPNs. It is also classified under the symmetric key algorithm and this is implemented by the use of a single key for encryption and decryption. AES has defined the key size of 128, 192, and 256 bits and is most secure among all with AES 256. It is quite safe to work with this algorithm with the efficient protection against the brute force attacks (Marinakis, 2021). Some VPN protocols currently employing AES are IPsec, OpenVPN, L2TP among others.
3DES (Triple Data Encryption Standard): 3DES is a reliable and older version of encryption which is better than DES algorithm, it applies DES algorithm three times using three different keys. Although relatively more secure in comparison to DES, 3DES is slower and less efficient than AES algorithm and is still used occasionally in older VPN technologies, yet has been withdrawn from commonly used algorithms of VPN technologies due to the issues of security and performance.
Blowfish: Blowfish is a symmetric encryption algorithm and it works on a 64 bits of data block. It is fast and reliable on occasion, which is why it is used frequently in connection with VPNs. Blowfish has key sizes up to 448 bits thus making it offer strong encryption (Pathak et al., 2022). However, it has been increasingly replaced by AES in most contemporary VPN implementations because of its better security and speed.
Reference List
Marinakis, A., 2021. A Systematic Comparison of Default based Versus Hardened IoT Systems Using Honeypots: Master Thesis| Supervisor: Maria Papadaki.
Pathak, P., Jaiswal, M.R., Gupta, M.K., Sharma, S. and Singhnayak, R., 2022. Leveraging research honeypots for generating credible threat intelligence and advanced threat analytics. In Implementing Enterprise Cybersecurity with Opensource Software and Standard Architecture (pp. 67-110). River Publishers.
Activity 8.10: Designing an Integrated Security System
Integrated System for Securing a Medium-Sized Company
That protection of the medium-sized company requires a set of measures that include the range of the security systems used. It is the task to ensure the company’s internal network as well as the external networks are secure. Here is an integrating plan of security that complements multiple security aspects as well as uses technologies in aiding the security objective.
Network Security: Firewalls and IDS/IPS
The first line of defense for the company may include firewalls as well as the Intrusion Detection System (IDS) or Intrusion Prevention System (IPS). Anti-virus programs would be used to filter the traffic flow in and out of the local networks to prevent unauthorized communication. NIDS/NIPS is also known as Network-based IDS/IPS that can be used with collective objectives of watching the network traffic or particularities of the traffic, malware and attacks (Morozov et al., 2023). These systems are valuable to identify and prevent possible intrusions instantaneously so as to safeguard the inner network of the company. In the organization's internal network, there is the Host-based IDS/ IPS (HIDS// HIPS) that can be installed on individual workstations. These systems will track and audit the hosts, allow access to files, system and application call and run, to prevent user machines potentially compromising the network.
Data Encryption and Secure Communication
To maintain confidentiality and integrity of data, only VPN with strong encryption like AES will be utilized. VPNs will act as a means of communication for the employees who are working remotely or other branch offices in the future and then encrypt the data passed over the internet connection (Aydın, 2021). The SSL/TLS encryption of web traffic will also protect HTTP connection by providing a method of ensuring that any information transmitted over the browser is not intercepted by other parties.
Authentication and Access Control
In order to prevent data breaches and unauthorized access the information system will incorporate MFA for the main applications and organizational systems. MFA that involves the use of at least two identity proofing factors will greatly minimize the chances of unauthorized accessMapped RBAC will be adopted to ensure that employees are allowed access only to resources relevant to their roles.
Endpoint Security and Malware Protection
It is important to protect end-user devices employed by employees in organizations due to manifold reasons. This involves setting up antivirus and anti-malware applications on all the points of connection (computers, laptops, mobiles). They will work without ceasing and perform scans of the used network for presence of malicious software with the purpose of preventing it from penetrating within the network (Shikhaliyev, 2023). The security features will also include weekly patch management to ensure a periodic update of the security patches of all the devices.
Backup and Disaster Recovery
The online backup and disaster recovery will be established so as to be used when there is an attack or any disaster that affects the company. The key data will be backed up on a more frequent, manual and encrypted basis and kept off-site or preferably, off-site cloud storage. It enables the company to easily restore data in the systems in the event that they are harmed or corrupted.
Employee Training and Awareness
Human factors are still frequently cited as one of the key areas of concern for cybersecurity. Hence, he or she initiated the enhancement of cybersecurity training in the company that will cover all the employees. The training is going to involve identification of phishing emails, the importance of secure passwords, and safe use of the internet. In this report, they argue that it is central to cultivating security awareness and making certain that human behavior cannot be used as an approach that would lead to a successful attack on the organization.
Reference List
Morozov, D.S., Vakaliuk, T.A., Yefimenko, A.A., Nikitchuk, T.M. and Kolomiiets, R.O., 2023, April. Honeypot and cyber deception as a tool for detecting cyber attacks on critical infrastructure. In doors (pp. 81-96).
Aydın, K., 2021. Analysis of Password Attacks From the Perspective of the Attacker by Multiple Honeypots (Master's thesis, Middle East Technical University (Turkey)).
Shikhaliyev, R.H., 2023. Cybersecurity analysis of industrial control systems. Problems of Information Society, pp.47-54.
Reference List
Journals
- Aradi, Z. and Bánáti, A., 2025, January. The Role of Honeypots in Modern Cybersecurity Strategies. In 2025 IEEE 23rd World Symposium on Applied Machine Intelligence and Informatics (SAMI) (pp. 000189-000196). IEEE.
- Trisolino, A., 2023. Analysis of Security Configuration for IDS/IPS (Doctoral dissertation, Politecnico di Torino).
- Sharma, D.S., 2024. Enhancing False Positive Detection in IDS/IPS Using Honeypots: A Case Study with CSE-CIC-2018 Dataset [online]
- Franco, J., Aris, A., Canberk, B. and Uluagac, A.S., 2021. A survey of honeypots and honeynets for internet of things, industrial internet of things, and cyber-physical systems. IEEE Communications Surveys & Tutorials, 23(4), pp.2351-2383.
- Franco, J.R., 2022. Honeypot-based Security Enhancements for Information Systems.
- Achari, A., 2024. Advanced Cybersecurity Tactics. Educohack Press.
- Luntovskyy, A., 2023. Advanced Networking and Cybersecurity Approaches. In Reliability Engineering and Computational Intelligence for Complex Systems: Design, Analysis and Evaluation (pp. 79-98). Cham: Springer Nature Switzerland.
- Athukorale, N.K., Yi, C.J., Loh Zi Xin, A.Y., Qi, C.J., Yu, D.Z., Wei, J.S.J., Hady, F., Zhe, L.S., Eu, C.C. and Sindiramutty, S.R., 2025. Evaluating Advanced Cybersecurity Technologies for Cloud Environments.
- Rabiul Hasan, M., 2024. Safeguarding of Financial Organization from Cyber-Attack using Next Generation Firewall (NGFW), Security Information & Event Management (SIEM) and Honeypot (Doctoral dissertation, Dublin Business School).
- Raghul, S.A., Gayathri, G., Bhatt, R. and Kumar, K.V., 2024, June. Enhancing cybersecurity resilience: Integrating ids with advanced honeypot environments for proactive threat detection. In 2024 3rd International Conference on Applied Artificial Intelligence and Computing (ICAAIC) (pp. 1363-1368). IEEE.
- Yang, X., Yuan, J., Yang, H., Kong, Y., Zhang, H. and Zhao, J., 2023. A highly interactive honeypot-based approach to network threat management. Future Internet, 15(4), p.127.
- El Kouari, O., Lazaar, S. and Achoughi, T., 2025. Fortifying industrial cybersecurity: a novel industrial internet of things architecture enhanced by honeypot integration. International Journal of Electrical & Computer Engineering (2088-8708), 15(1).
- Chairopoulou, S., 2024. Cybersecurity in industrial control systems: a roadmap for fortifying operations (Master's thesis, Πανεπιστήμιο Πειραιώς).
- Albinsson, F. and Riedl, J., 2021. HONEYPOT–To bee or not to bee: A study of attacks on ICS/SCADA systems.
- Abhijith, R. and Kumar, B.S., 2021, May. First Level Security System for Intrusion Detection and Prevention in LAN. In 2021 2nd International Conference for Emerging Technology (INCET) (pp. 1-5). IEEE.
- Rana, M. and Patil, J., 2025. Fortifying Cyber Defenses: Leveraging Honeypots for Proactive Threat Mitigation and DoS Attack Prevention. International Journal of Computer Science & Communications (IJCSC), 10(1), pp.1-16.
- Kelly, C., Pitropakis, N., Mylonas, A., McKeown, S. and Buchanan, W.J., 2021. A comparative analysis of honeypots on different cloud platforms. Sensors, 21(7), p.2433.
- Marinakis, A., 2021. A Systematic Comparison of Default based Versus Hardened IoT Systems Using Honeypots: Master Thesis| Supervisor: Maria Papadaki.
- Pathak, P., Jaiswal, M.R., Gupta, M.K., Sharma, S. and Singhnayak, R., 2022. Leveraging research honeypots for generating credible threat intelligence and advanced threat analytics. In Implementing Enterprise Cybersecurity with Opensource Software and Standard Architecture (pp. 67-110). River Publishers.
- Morozov, D.S., Vakaliuk, T.A., Yefimenko, A.A., Nikitchuk, T.M. and Kolomiiets, R.O., 2023, April. Honeypot and cyber deception as a tool for detecting cyber attacks on critical infrastructure. In doors (pp. 81-96).
- Aydın, K., 2021. Analysis of Password Attacks From the Perspective of the Attacker by Multiple Honeypots (Master's thesis, Middle East Technical University (Turkey)).
- Shikhaliyev, R.H., 2023. Cybersecurity analysis of industrial control systems. Problems of Information Society, pp.47-54.