- Introduction Of Penetration Testing Report Assignment
- Activity 7.1: Checklist for Penetration Testing
- Activity 7.2: Advanced Persistent Threat (APT)
- Activity 7.3: Scenario-Based Penetration Testing
- Activity 7.4: Suitable Tools for Penetration Testing
- Activity 7.5: Penetration Testing Legal Contracts
- Activity 7.6: Importance of Penetration Testing
- Activity 7.7: Planning Penetration Testing
- Activity 7.8: Company Perspective on Penetration Testing
Introduction Of Penetration Testing Report Assignment
Activity 7.1: Checklist for Penetration Testing
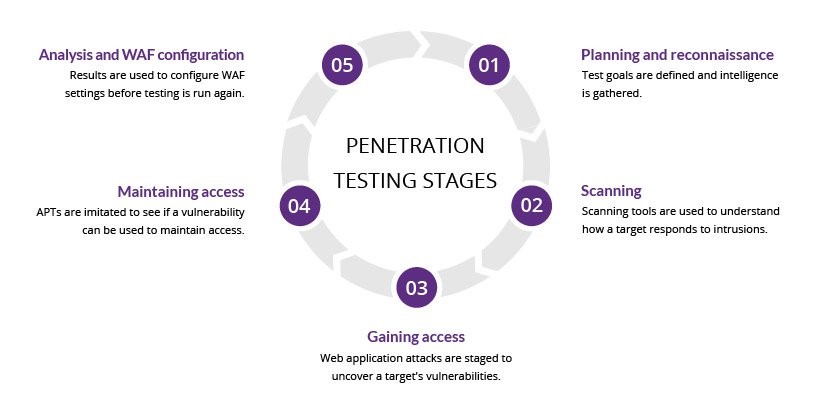
Figure 1: Penetration Testing
Internal Penetration Testing
Internal penetration testing deals with testing the security of internal network infrastructure of the bank. This is done through network security such as open ports scanning, firewall and access control, simulations of emails, application security and attacks such as privilege escalation and data security, where it checks for secure storage of data and encryption.
External Penetration Testing
External penetration testing can be defined on the basis of assessing vulnerabilities from an outside perspective. Specific concerns comprise of perimeter defense some organizations opt to test firewalls and IDS systems, web application security to check for cross site scripting or DoS/DDoS to confirm how the bank can handle interruption of its services, password cracking to assess password protection, and public exposure, where some company information are searched on the internet.
Focus on External Penetration Testing
Since the external threat is more significant, there is more significance that should be placed on the external penetration testing. From the two systems, it is prudent that the bank’s external structure, such as web applications and the online banking services are at a high risk of attack by a cybercriminal (Happe and Cito, 2023). Adequate protection of the organization from external threats minimizes chances of intrusions, data compromises, or even service discontinuity, thus there is a need to incorporate external testing.
Assignment deadlines piling up? Let New Assignment Help ease your burden with expert Assignment Help UK tailored for student success.
Activity 7.2: Advanced Persistent Threat (APT)
Advanced Persistent Threats (APTs) are long-term, strategic and strategic invasions and intrusions which are caused by knowledgeable and skilled attackers including state-sponsors or restrained groups of attackers. In contrast to regular attack patterns, APTs are much more interested in continually accessing the organizations of their choice and remaining stealthy for long periods.
Differences between APTs and Regular Attacks
| Factor | APT | Regular Attack |
| Target | Specific organizations | Random individuals or businesses |
| Duration | Long-term (months/years) | Short-term (minutes/days) |
| Attack Methods | Stealthy and persistent | Quick and opportunistic |
| Motivation | Espionage, data theft | Financial gain, disruption |
Table 1: Difference table
Impact of APTs on Penetration Testing
Solo’s presence implies that an organization has to make changes to its testing approaches to accommodate APTs. White-box penetration testing emerges as crucial since one needs to establish internal vulnerabilities that might be exploited. Lastly, real time monitoring and incident response tests must also be established to determine how ready the security team is in detecting and responding to the presence of APT (Wilhelm, 2025). Since APT attacks should mimic the true to life threats their simulations should include zero-day vulnerability, social engineering and privilege escalation.
Activity 7.3: Scenario-Based Penetration Testing
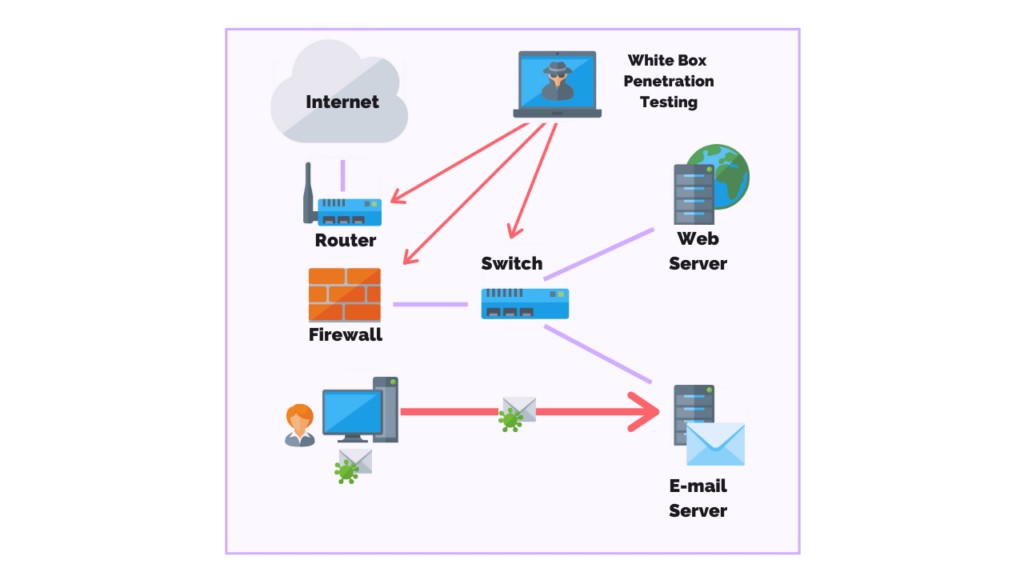
Figure 2: Penetration Testing
Compromised Employee Credentials
This particular scenario focuses on the consequences facing an organisation when an attacker is able to compromise an employee’s login details. The purpose of the test is to determine how far an attacker can go in penetrating a system before it is noticed (Elsharef, 2021). Thus it aids in making weak points in authentication, access control and detection mechanisms felt during unauthorized penetration, clear.
Malicious Insider Attack
In this case, an internal employee with authorized access to such information takes advantage of vulnerabilities. The test ascertains the compliance of the organization’s access control, monitoring, and detection on preventing such threats (Semenov et al., 2021). It will be beneficial to help organizations improve internal controls, prevent providing users with more access than required, and monitor systems to avoid data abuse.
Web Application Exploitation
In this particular scenario, the clients should determine threats associated with customer interface applications including online banking facilities. SQL injection and cross site scripting (XSS) used to check whether or not the given data can be manipulated hence leading to violation of data security. The overall presentation of this simulation is to establish a model for the organizations to review in an effort to address the vulnerabilities that exist in application security to enhance customer information protection against external threats (Nixon, 2021). Each of the following scenarios gives an idea about the loophole that can be exploited and how an organization based on the situation can go about rectifying it to enhance their security system.
Activity 7.4: Suitable Tools for Penetration Testing
Recommended Tools for Penetration Testing
| Type of Testing | Tools | Purpose |
| Internal Testing | Wireshark | Monitors and analyzes network traffic. |
| Metasploit | Exploits system vulnerabilities. | |
| External Testing | Nmap | Scans for open ports and network services. |
| Acunetix | Detects web application vulnerabilities. |
Table 2: Different tools table
Checklist for Tool Selection
There are certain criteria that should be met to identify the appropriate tools for penetration testing to avoid incongruity. When dealing with internal and external tests, it is very important to reduce false positive and false negative results. The compatibility with the organization’s infrastructure such as operating systems current networks should also be considered. With regard to the tools, there should be an ability to automate the vulnerability scanning and the reports. Legal conduct of testing is achievable under such laws as GDPR and ISO 27001 regulations. Moreover, tools have to have highly effective reporting so that results received can be easily documented (Sofyan et al., 2023). Finally, it is established that tool availability in the community increases its reliability against new threats.
Activity 7.5: Penetration Testing Legal Contracts
The legal contracts of Penetration testing must be designed to define all the legalities of the risk assessment including the scope, responsibilities, and limitations for the assessment. The purpose of these documents is to act as legal measures that will guarantee that any test conducted by the penetration testing firm meets the legal requirements of the client firm (Tassava et al., 2024). Precisely, and clearly drafted legal frameworks, help in avoiding risk associated with testing and protect each party ought to conduct testing ethically and securely.
Key Components of a Penetration Testing Contract
Testing Boundaries - The organization should also define in the contract what systems, applications, and even the networks to be tested. It should also limit the spread of the test in order to avoid checking on other structures that are not important in the assessment.
Non-Disclosure - To make sure that all the findings, vulnerabilities, or specific details observed in testing can be kept secret then a Non-Disclosure Agreement (NDA) needs to be incorporated. This leaves out the sharing or misuse of loopholes by those persons that are not supposed to use it.
Testing Limitations and Restrictions - Some of the areas in an organization could be restricted from testing to avoid affecting the day to day running of the organization, for instance, the live production environment may not allow testing (Arbianto and Yuono, 2021). Such risks must be stated on the contract so that they do not bring about undesirable effects in the future as considered here under.
Regulatory Requirements - It should be cleared the legal requirements like GDPR, ISO 27001, national cybersecurity regulation for all the testing activities performed in the contract or the agreement. This is especially true because the data managed by such an organization may be sensitive to the users.
Liability and Insurance and of Risk - If the penetration testing leads to a system disruption or loss of data put down as to who is liable. Specific agreements may contain provisions that specify that penetration testing firms need to also carry out cyber liability insurance.
Data Protection and Privacy Considerations
This is because penetration testing requires one to deal with important information, and legislation on the protection of data must be respected at all times. It is required that a penetration tester does not copy, alter or transmit any customer information in any way that is not permitted (Sultan and Abbas, 2021). There needs to be provisions within the contract required data handling procedures, how long data should be retained and provisions for data disposal after testing and analysis to avoid leakage of the data.
Activity 7.6: Importance of Penetration Testing
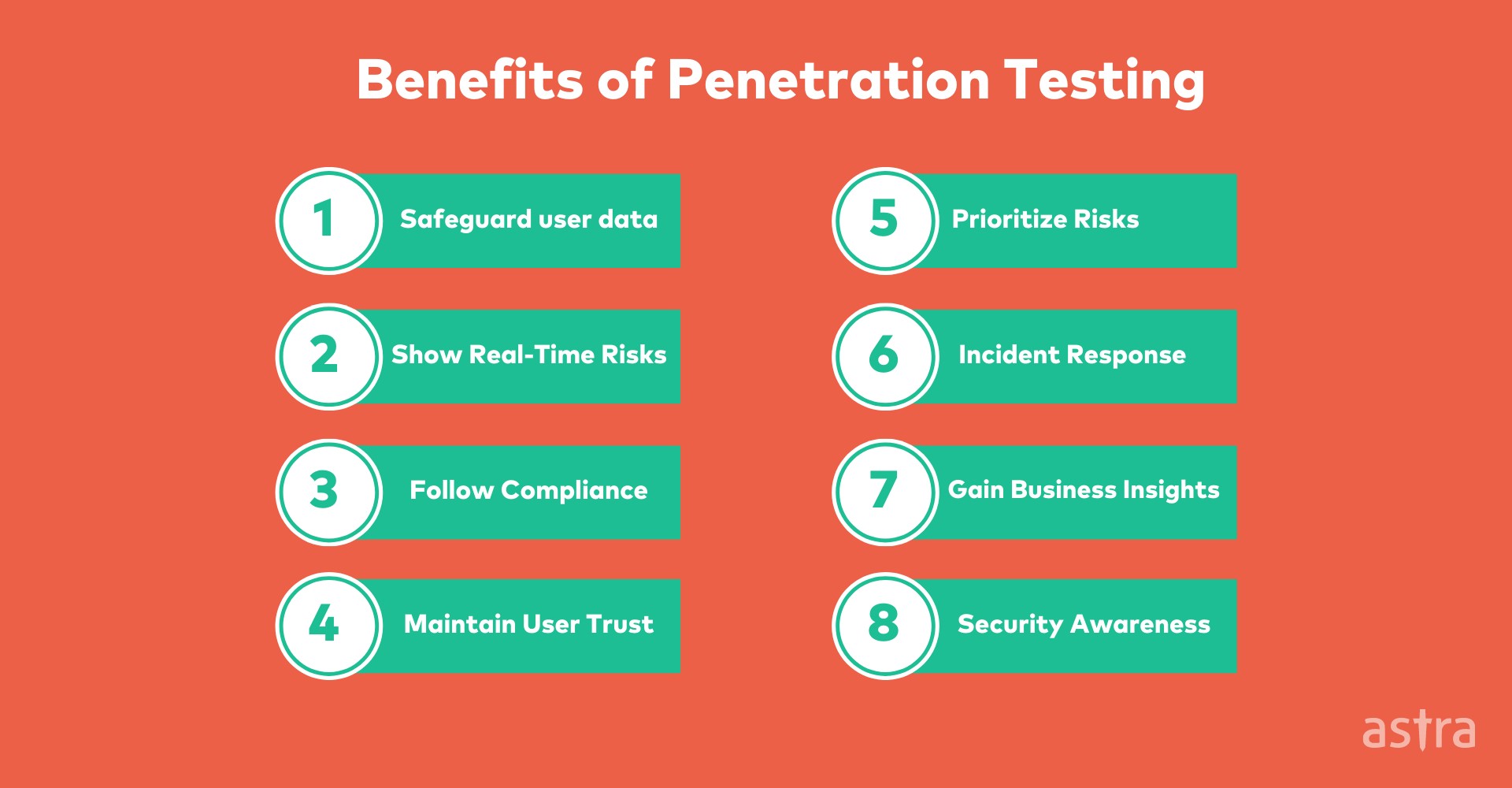
Figure 3: Penetration testing benefits
Penetration testing is an essential activity in cybersecurity since it can help in uncovering how the attackers can infiltrate the organization’s systems. The negative implications that originate from the avoidance of penetration testing include embezzlement, leakage of crucial information, fines and penalties among others especially within a banking environment where time is usually not on the side of the testing teams and institutions (Zhang et al., 2021). Thus, the security assessments should be performed for a new product to safeguard the organization and the customers who will use the product.
Arguments for Conducting Thorough Penetration Testing
Small considerations - Banks need to follow various protection rules including GDPR, PCI-DSS and the FCA in the United Kingdom. Penetration testing is also effective in ensuring that institutions operate within the standards set by the law to avoid cases of fines or even legal proceedings.
Risk Management - Invulnerable areas must be pointed out before the attackers see it useful to exploit them. An example of a threat associated with the application is that of an attacker obtaining users’ sensitive information, initiating unauthorized transactions, and tarnishing the image of the bank.
Proposed Penetration Testing Strategy
- Black-Box Testing: Makes the assumption of the target system by mimicking different external threats with the assumption of the latter being open to the public.
- White-Box Testing: Refers to the security testing that aims at exploiting internal vulnerabilities of a program through the analysis of the code and structure of a particular application.
- This technique is done to determine the extent to which an attacker can penetrate a system through gained or stolen credentials.
Activity 7.7: Planning Penetration Testing
Ethical Considerations in Penetration Testing
Ethical penetration testing means that very specific ethical standards have to be followed in order to ensure that the security tests are done in a legal and proper manner. It is very important to seek permission from the organization to conduct the tests before commencing the exercise. The concerns that the penetration testers should consider include; they should conduct tests in hours that will minimize disruption of the business (Han et al., 2022). There is also privacy to preserve; any discovered weaknesses should also not be known to anyone else or other parties.
Differences between Internal and External Penetration Testing Ethics
| Ethical Aspect | Internal Testing | External Testing |
| Consent | Required from management | Requires legal contract |
| Data Sensitivity | Higher risk of exposing company secrets | Focuses on public-facing vulnerabilities |
| Testing Scope | Covers internal networks | Limited to external threats |
Table 3: Difference table
Activity 7.8: Company Perspective on Penetration Testing
As an IT administrator, it is essential to consider the strategies and steps of hiring an external penetration testing firm for security, compliance, and operations. As crucial as penetration testing is to reveal various vulnerabilities, it poses specific risks including, leakage of data and disruption of the system. These concerns can only be dealt with by signing an iron clad contract so as to bring the required control over the testing.
Main Concerns in Hiring an External Penetration Testing Agent
Confidentiality and Data Security
One of the major issues that should be considered while outsourcing an organization’s pen testing to an external firm is security and privacy. Non-disclosure agreements should be made on the issue of security findings in order to ensure that such information is not shared by an unauthorized person (Bahrami et al., 2021). Also, the work of a testing firm must state that the company cannot store any data after the testing process is over to continue preserving the confidentiality of information that was shared during and after the process.
Scope and Testing Limitations
However, it becomes crucial to establish the boundaries of the penetration test which are, in fact, the limit of the attack that can be carried out to avoid interference with other processes. The test scope needs to identify which systems, networks, and applications are to be included and those not be tested as this will not affect the critical business applications that deal in real time operations thereby leading to system loss or operational complications.
Compliance with Data Protection Laws
There are certain testing laws and regulations that could be followed by the testing firm like GDPR and ISO 27001. To this extent, the contract should include guidelines that favours the legal rules governing the collection and storage of data to prevent exposing sensitive information belonging to the organisation.
Reference List
Journals
- Happe, A. and Cito, J., 2023, November. Getting pwn’d by ai: Penetration testing with large language models. In Proceedings of the 31st ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering (pp. 2082-2086).
- Wilhelm, T., 2025. Professional penetration testing: Creating and learning in a hacking lab. Elsevier.
- Semenov, S., Weilin, C., Zhang, L. and Bulba, S., 2021. Automated penetration testing method using deep machine learning technology. Advanced Information Systems, 5(3), pp.119-127.
- Nixon, I.K., 2021. Standard penetration test State-of-the-art report. In Penetration Testing, volume 1 (pp. 3-22). Routledge.
- Sofyan, H., Sugiarto, M. and Akbar, B.M., 2023. Implementation of Penetration testing on Websites to Improve Security of Information Assets UPN" Veteran" Yogyakarta. Telematika: Jurnal Informatika dan Teknologi Informasi, 20(2), pp.153-162.
- Tassava, M., Kolodjski, C., Milbrath, J. and Straub, J., 2024. Enhancing Security Testing Software for Systems that Cannot be Subjected to the Risks of Penetration Testing Through the Incorporation of Multi-threading and and Other Capabilities. arXiv preprint arXiv:2409.10893.
- Arbianto, R. and Yuono, T., 2021. Comparison of California bearing ratio (CBR) value based on cone penetration test (CPT) and dynamic cone penetrometer (DCP). Comparison of California Bearing Ratio (CBR) Value Based on Cone Penetration Test (CPT) and Dynamic Cone Penetrometer (DCP), 4(2), pp.70-78.
- Sultan, H.M.K.M.M. and Abbas, A.F., Enhance Penetration Testing Techniques to Improve Cybersecurity with NetLogo, Nmap, and Wireshark. Journal of Natural and Applied Sciences URAL, p.100.
- Zhang, Y., Wu, J., Wang, D. and Zhang, S., 2021, December. Research and application of penetration testing method in industrial control system. In International Conference on Electronic Information Engineering and Computer Technology (EIECT 2021) (Vol. 12087, pp. 86-92). SPIE.
- Bahrami, M., Naderi-Boldaji, M. and Ghanbarian, D., 2021. Development and Calibration of a Discrete Element Model for Penetration Test in Cohesive Soil. Iranian Journal of Biosystems Engineering, 52(4), pp.613-633.
- Han, Y., He, K. and Shao, W., 2022. Research on Standardization of Test Document Set Based on Automotive Penetration Test. World Scientific Research Journal, 8(11), pp.280-284.
- Elsharef, R.R., 2021. Design of a Novel Manual and Automated Penetration Testing Framework for Connected Industrial Control Systems (ICS) (Doctoral dissertation, The University of Wisconsin-Milwaukee).

