- Introduction Of Network Cisco Packet Tracer Assignment
- Background
- Requirements Analysis
- Departmental Overview
- Connectivity Needs
- Security Considerations
- Network Design Overview
- Architectural Overview
- Device Selection
- IP Addressing Scheme
- Subnetting Approach
- IP Allocation
- IP allocation of the managers
- Security Implementation
- Password Policy
- Firewalls
- Device Configuration
- Implementation
- Network Diagram
- Packet Tracer Model
- Testing and Validation
- Analysis
- Strengths of the Design
- Areas for Improvement
Introduction Of Network Cisco Packet Tracer Assignment
TechnoLink Solutions, a small but fast-growing firm, is in the process of moving from its current multi- storey structure and leasing a single story office building that will enhance overall workflow. As a result of fast-paced business processes, it is now necessary to organize a reliable, safe, and scalable network in the new location. This paper presents an elaborate network design that will suit the organization by fulfilling the modern standards in networking. This solution is the use of wired and wireless connections, the protection of the network from intruders and the possibility of effective communication between all departments and employees. The key tasks include:
- Network Diagram of the design that has been proposed.
- A scheme of IPv4 address that includes the subnetted address such as 192.168.10.0/24 and 192.168.11.0/24.
- All aspects involving security such as the setting up of devices and or firewalls.
- Implementation of the network in Cisco Packet Tracer.
- Functionality and connectivity test outputs which confirm the performance of the network.
This paper seeks to give a clear explanation of the design decisions and the implementation plan towards creating a reliable and an efficient networking environment for TechnoLink Solution.
Say goodbye to academic pressure! New Assignment Help is your go-to partner for expert-level Best Assignment Help in the UK.
Background
TechnoLink Solutions, a client oriented organization with a distinct recognition of the importance of innovation, is in the process of a strategic move to a single story office building. This has the potential to create room for the adoption of new, current and future fit networking solutions for the organization (Balyk et al. 2022). Due to the six departments, individual managerial offices and the reception area the cabling has to be both wired and wireless in order to support the functionality of the office. The complicated and manifold are the network requirements for TechnoLink Solutions. All departments depend on Internet connectivity, the exchange of files, and interaction between departments to perform their tasks. Moreover, the widespread use of laptops for mobility necessitates reliable Wi-Fi coverage across the premises (Mishra et al. 2022). Because some departments may be larger than others, and because people may carry around mobile devices with access to the network, the design of the network must be able to meet the needs of both small groups and large groups of organization members. Recent trends of networking focus on the possibilities of networking scalability, security, and optimal usage of network resources. Mainly, using subnetting and VLANs, and combining with improved routing protocols, the design can help provide secure connections and efficient data transfers between departments (Santyadiputra et al. 2021). Furthermore, integrating wireless access points (APs) with the latest Wi-Fi specifications ensures wireless mobile users connectivity is not interrupted. The use of enhanced forms of security measures, and firewalls greatly guards the network against possible hazards, thus maintaining the credibility and the secrecy of the information. This background seeks to give TechnoLink Solutions a clear view of how they can put in place an excellent network that caters for its operations (Ahmed and Al-Hamadani, 2021). This discussion is informed by a literature review of current networking trends including wired and wireless connectivity, subnetting and security.
Requirements Analysis
Departmental Overview
The office design has six functional areas that are departments and four other offices that are senior management related offices and reception. Every department has certain connectivity needs that need to be met in order for everything to run efficiently (Allison, 2022). The distribution of the staff and the devices are clearly described by the following table:
| Department | Staff Count | Devices (Desktops) | Laptops |
| Product Development | 22 | 22 | 1 |
| Marketing | 18 | 18 | 1 |
| Customer Support | 15 | 15 | 1 |
| IT Support | 8 | 8 | 1 |
| Human Resources | 6 | 6 | 0 |
| Accounting | 7 | 7 | 1 |
| Reception | 5 | 5 | 0 |
Rest Laptops are distributed across the departments for mobility, meeting, as well as for presenting to clients. These devices must be supported by the network, wired and wirelessly.
Connectivity Needs
TechnoLink Solutions requires a network that ensures:
- Internet Access: Every staff must require their own or office internet connectivity for their official works.
- Wi-Fi Coverage: Mobile planners should ensure that the wireless access points can support the mobility of its users fully.
- File Storage: Centralized file storage should be able to enable access to common files by many departments within an organization and ensure that security is created for those resources that are shared in a central location (Bwalya and Zimba, 2021).
- Inter-Department Communication: Group communication is crucial with having to keep the various departments’ exchanges efficient and secure.
Security Considerations
The security consideration is a significant factor while designing the network. The proposed solution includes:
- Password-protected access for all devices and management interfaces.
- Encryption of the content for protection of sensitive data in motion and in storage.
- Firewalls for the purpose of limiting access to the network and controlling traffic.
Network Design Overview
Architectural Overview
The design of the network shall entail both wired and wireless network to suit the needs of all the departments as well as the organization at large. Routers and switches provide the connections, and access points, with properly subnetted IP addresses add security to the settings.
- Wired Connectivity: For the wired devices, the desktops and other devices in each department, there are managed switches. They can also be switched between interconnecting users with a core router used to handle communication between departments within an organization.
- Wireless Connectivity: The building is equipped with dual-band Wi-Fi 6 access point offering wireless connectivity at higher speed at specific locations (Podsadnikov et al. 2021). These access points allow connectivity on laptops and on portable devices to allow internet connectivity.
- Centralized Resources: A web host entails a dedicated server to store the files, the backups and hosting of the applications. This server can be accessed by any department in the wired and wireless networks in the organization.
Device Selection
The following devices are used in the network:
- Routers: The subnet routing as well as the external connectivity is managed using CISCO Integrated Services Routers (ISR) known as routers.
- Switches: Proper internal communication is made possible through the use of Managed Layer 2/3 switches.
- Access Points: The wireless connection offers trustworthy Wi-Fi 6 access points with dual bands.
- Firewall Appliance: Cisco ASA firewall is used as the security shield against the outside world.
IP Addressing Scheme
Subnetting Approach
IPv4 addresses 192.168.10.0/24 and 192.168.11.0/24 are subnetted according to the department’s size and anticipated future development. Every department is given its own subnet in order to restrict mobility and for ease of management.
IP Allocation
| Subnet | IP Range | Subnet Mask |
| Product Development | 192.168.1.2 - 192.168.1.6 192.168.1.42 - 192.168.1.58 | 255.255.255.0 |
| Marketing | 192.168.1.59 - 192.168.1.71 192.168.1.8 - 192.168.1.12 | 255.255.255.0 |
| Customer Support | 192.168.1.14 - 192.168.1.18 192.168.1.72 - 192.168.1.81 | 255.255.255.0 |
| IT Support | 192.168.1.20 - 192.168.1.24 192.168.1.82 - 192.168.1.84 | 255.255.255.0 |
| Human Resources | 192.168.1.26 - 192.168.1.30 192.168.1.85 | 255.255.255.0 |
| Accounting | 192.168.1.86 - 192.168.1.87 | 255.255.255.0 |
| Reception | 192.168.19.2 - 192.168.19.6 | 255.255.255.0 |
Every subnet is planned according to today’s number of connected devices with some capacity to incorporate additional equipment in the future. IP Allocation of LAN/ wifi
| Subnet | IP Range | Subnet Mask |
| Product Development | 192.168.1.1 | 255.255.255.0 |
| Marketing | 192.168.1.7 | 255.255.255.0 |
| Customer Support | 192.168.1.13 | 255.255.255.0 |
| IT Support | 192.168.1.19 | 255.255.255.0 |
| Human Resources | 192.168.1.25 | 255.255.255.0 |
| Accounting | 192.168.1.31 | 255.255.255.0 |
| Reception | 192.168.19.1 | 255.255.255.0 |
IP allocation of the managers
| Subnet | IP address | Subnet Mask |
| Product Development Manager | 192.168.1.38 | 255.255.255.0 |
| Marketing Manager | 192.168.1.42 | 255.255.255.0 |
| Customer Support | 192.168.1.43 | 255.255.255.0 |
| IT Support | 192.168.1.39 | 255.255.255.0 |
| Accounting | 192.168.1.41 | 255.255.255.0 |
Security Implementation
Password Policy
As standard measures to increase the networks’ security, all devices in the network have complex passwords encrypted by default. A universal password, '@Networks2425’, is set and documented for configuration and only for the administration purposes.
Firewalls
A Cisco ASA firewall is configured to:
- Block unauthorized traffic.
- Advise only specific access to the internet by the subnets.
- Maintain close attention to all entering and exiting information searching for irregularities.
Device Configuration
The following measures are implemented for all routers and switches:
- Hostname Configuration: Devices are renamed based on the function they perform to make identification easy, and they include Router 1 and Switch-Sales.
- Banner Message: Unauthorized users are warned by a message known as Message of the Day (MOTD).
- Password Encryption: All passwords are encrypted with the options inherent in the Cisco system security.
Below is an example configuration for a router:
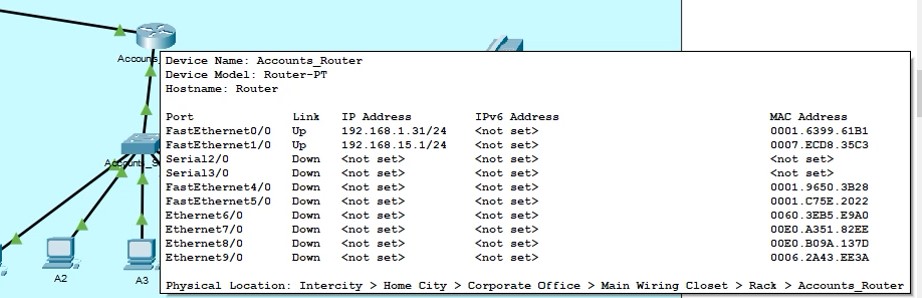
Figure 1: Example configuration
Implementation
Network Diagram
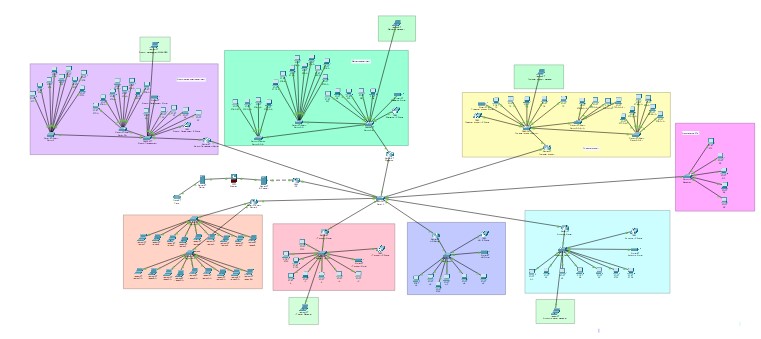
Figure 2: Network design of the TechnoLink Solutions
Packet Tracer Model
Using Cisco Packet Tracer, the whole network is designed to verify and then implement the design. Some are applied to ensure that while others are applied to ensure that.
- Every device in its subnet works well together.
- There is order and security in inter and intra communication between departments.
- Internet connection is facilitated on all the devices.
Testing and Validation
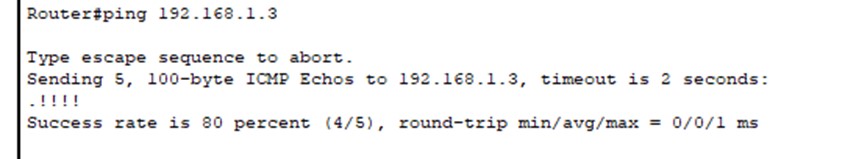
Figure 3: Ping test between router and product department PCs
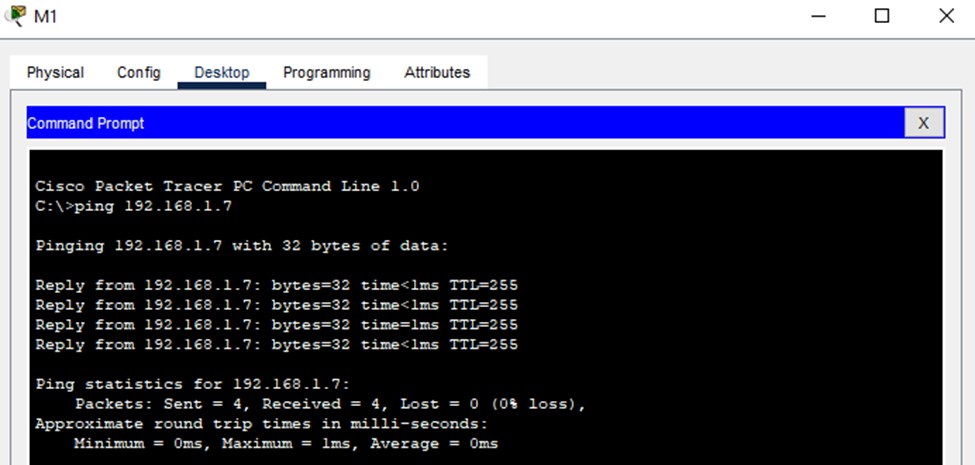
Figure 4: Ping test between the marketing department PCs and router
Figure 5: Ping test between two PCs in marketing department
Ping tests are performed a number of times for interoperability between the devices that belong to different subnets. With such successes in communication result, the IP addressing scheme and routing configuration are thus vindicated.
Analysis
The current structure of the network design for TechnoLink Solutions provides the technology element for reliability, security, and scalability principles as seen in today’s technological advancements. The following outline presents an assessment of some of the essential elements of the design and how organisational learning could benefit from it as well as the areas of improvement.
Strengths of the Design
- Scalability: Subnetting and VLANs guarantee the future growth of the organization’s network capacity. Every department has its subnet which creates the opportunity to add extra devices without rewiring the whole network.
- Security: Firewalls, b passwords with encryption, WPA3 offers formidable defense mechanisms against internal and external invasions. More specifically VLANs add another layer of isolation to the securely safeguarding of sensitive traffic data.
- Performance: External cabling gives stable and high speed wired connectivity for desk tops, whereas wireless connectivity for mobile clients is via Wi-Fi 6 access point (Muhammad and Munir, 2023). Static routing and dynamic routing improve the transferral of information by minimizing the amount of time taken and traffic density.
- Cost-Effectiveness: It also uses easily accessible technologies and equipment where initial investment is not too high but the organizational requirements are met satisfactorily.
Areas for Improvement
- Redundancy: It also does not address failover mechanisms for other important devices at the current design. Redundant routers and switches means that even in case of hardware breakdown there is another existing to take the place of the default one.
- Monitoring and Management: The inclusion of extra instrumentation in the network like SolarWinds or Cisco DNA Center make it possible to get insights of the network performance and security immediately, thus making it easier to solve problems as soon as possible.
- Future Upgrades: However, in the current state, it is still possible to scale up the design where adopting SDN or network automation can help with the future scalability of the designs.
The TechnoLink Solutions’ network design proposed is a hybrid, where wired and wireless technologies are incorporated to meet the needs of the company. Every department receives its own subnet based on the managers proposed IPv4 ranges 192.168.10.0/24 and 192.168.11.0/24 (Alsheikhy, 2022). Subnetting helps in having an orderly manner of using the network addresses while reducing the instances that a large number of computers in a network broadcast messages making the network slow. Data cables are the primary physical connections in the design and offer both speed and reliability for the desks of several departments; for example, Product Development and Accounting (Muazu and Audi, 2021). Extendable wireless LANs are installed at different locations in the office to provide complete access to the mobile users such as the administration staff and managerial staff using laptops. The VLANs are used for increasing network segmentation where communication between departments is secure and efficient. For example, the Accounting information is protected from general traffic, and, thus, there is a limited chance to suffer from data leakage (Peca and Țurcanu, 2023). OSPF for instance is used in routing so that data gets to the right subnets in a network without getting lost. To avoid such threats, firewalls, passwords to encrypted form, and wireless protection according to WPA3 are used. Specifically, implementing a Cisco ASA firewall and intrusion prevention systems prevents unauthorized access and access with a specific type of malware. Passwords encrypted on routers and switches make it almost impossible for unwanted entities to access vital network infrastructure. Hence, the network design meets the operation needs of TechnoLink Solutions effectively making the solution secure, scalable and efficient (Gwangwava and Mubvirwi, 2021). The design incorporates up to date networking practices and technologies thus guaranteeing reliability of connectivity, a critical facet that makes the organization grow in terms of productivity.
Conclusion
The proposed network design would secure, reliable and scalable for TechnoLink Solutions connectivity throughout the organizational network design. This design shall have better networking technologies incorporated and shall meet universal BNT standards so as to improve productivity and accommodate growth.
Reference List
Journals
- Ahmed, A.H. and Al-Hamadani, M.N., 2021. Designing a secure campus network and simulating it using Cisco packet tracer. Indonesian Journal of Electrical Engineering and Computer Science, 23(1), pp.479-489.
- Allison, J., 2022, July. Simulation-based learning via cisco packet tracer to enhance the teaching of computer networks. In Proceedings of the 27th ACM Conference on on Innovation and Technology in Computer Science Education Vol. 1 (pp. 68-74).
- Alsheikhy, A., 2022. ESTIMATING END-TO-END DELAY ON A NETWORKING ENVIRONMENT USING A DEVELOPED FRAMEWORK. International Journal on Information Technologies & Security, 14(1).
- Balyk, N.R., Vasylenko, Y.P., Oleksiuk, V.P., Oleksiuk, O.R. and Shmyger, G.P., 2022. Cloud labs as a tool for learning Cisco CyberSecurity Operations and DevNet Associate Fundamentals courses. AET 2020, p.308.
- Bwalya, B. and Zimba, A., 2021. An SDN approach to mitigating network management challenges in traditional networks. International Journal on Information Technologies and Security, 13(4), pp.3-14.
- Gwangwava, N. and Mubvirwi, T.B., 2021. Design and simulation of IoT systems using the Cisco packet tracer. Advances in Internet of Things, 11(02), p.59.
- Mishra, A., Ghayar, J., Pendam, R. and Shinde, S., 2022. Design and implementation of smart home network using Cisco packet tracer. In ITM Web of Conferences (Vol. 44, p. 01008). EDP Sciences.
- Muazu, A.A. and Audi, I.U., 2021. Network configuration by utilizing cisco technologies with proper segmentation of broadcast domain in FNAS-UMYUK Nigeria. Journal of Network Security and Data Mining, 4(1), pp.1-13.
- Muhammad, T. and Munir, M., 2023. Network Automation. European Journal of Technology, 7(2), pp.23-42.
- Peca, L. and Țurcanu, D., 2023. Network security: Practical examples solved to be introduced in network security.
- Podsadnikov, A.V., Rozov, K.V. and Kratov, S.V., 2021, February. The methods and approaches to computer networks simulation using virtual network infrastructure. In Journal of Physics: Conference Series (Vol. 1791, No. 1, p. 012082). IOP Publishing.
- Santyadiputra, G.S., Listartha, I.M.E. and Saskara, G.A.J., 2021, March. The effectiveness of Automatic Network Administration (ANA) in network automation simulation at Universitas Pendidikan Ganesha. In Journal of Physics: Conference Series (Vol. 1810, No. 1, p. 012028). IOP Publishing.

